ABSTRACT
The performance of wireless networks is dependent on a number of factors including the available energy, energy-efficiency, data processing delay, transmission delay, routing decisions, security overhead, etc. Traditionally, due to limited resources, nodes were tasked with only collecting measurements and sending them to a base station or central unit for processing.
With increased capabilities of microprocessors the data processing is pushed more toward network and its more capable nodes. This thesis focuses to virtualize the processing resources of the entire network and dynamically distribute processing steps along the routing path while optimizing performance. Additionally, a new multi-key encryption (MKE) scheme is proposed to optimize efficiency while enhancing security. The main benefit of the MKE scheme is the improved resilience of the advanced encryption standard (AES) against correlation power analysis (CPA) attack by breaking the correlation between power consumption and the used secret key.
The MKE security scheme is analyzed with network implementation and studied for its effects on network parameters such as network connectivity, resilience against node capture and energy efficiency of the scheme. Moreover, a new analysis methodology is proposed to quantify a resilience of a network against node capture such that the strength of the underlying security mechanisms is taken into account. Furthermore, the trade-off between security and network performance is addressed by the proposed task-scheduling scheme.
Also, the proposed methodology does not make assumption of homogenous network that is often used in literature to simplify analysis and scheme design. In contrast, the proposed formulation is generic, thus allowing heterogeneous nodes to be used while guaranteeing network performance. Consequently, the proposed scheme creates a wireless “computing cloud” where the processing tasks are dynamically assigned to the nodes using the Dynamic Programming (DP) methodology. The processing and transmission decisions are analytically derived from network models in order to optimize the utilization of network resources including: available energy, processing capacity, security overhead, bandwidth etc. As a result, the online optimization of network resources is achieved.
A DYNAMIC PROGRAMMING APPROACH: IMPROVING PERFORMANCE OF THE WIRELESS NETWORKS
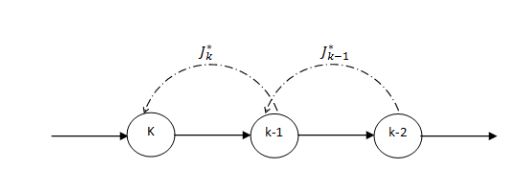
Fig 1. Feedback Mechanism of the Network
Fig 1 illustrates the feedback mechanism in the net work for communication for cost analysis. Nodes in the network communicate the necessary information for decision-making which is appended to ACK frames without the necessity of additional communication procedures. Nodes transfer necessary information that is vital for the cost analysis and should describe the cost-to-go terms sufficiently to make the optimal decision.
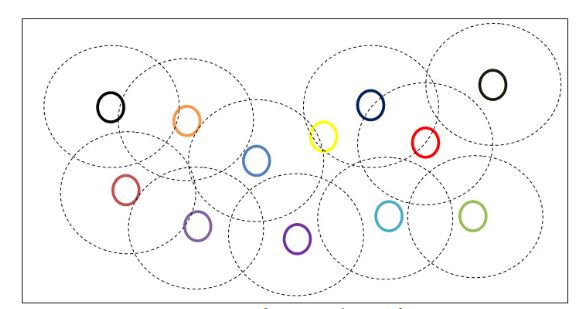
Fig 2. Example of Network Configuration
Fig 2 gives an idea of network topology with nodes placed in the network and indicated with the nodes transmitting ranges. Nodes communicate among the network with the help of neighboring nodes to transmit data packets.
ENERGY-EFFICIENT MULTI-KEY SECURITY SCHEME FOR WIRELESS SENSOR NETWORKS
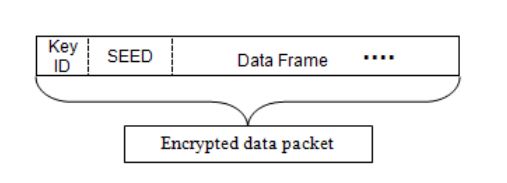
Fig 1. Data payload of a packet
The packet is encrypted such that only the destination node can decrypt the data with the corresponding shared keys. The original message is pre-pended with two fields: the first key ID and a seed, as shown in Fig. 1.
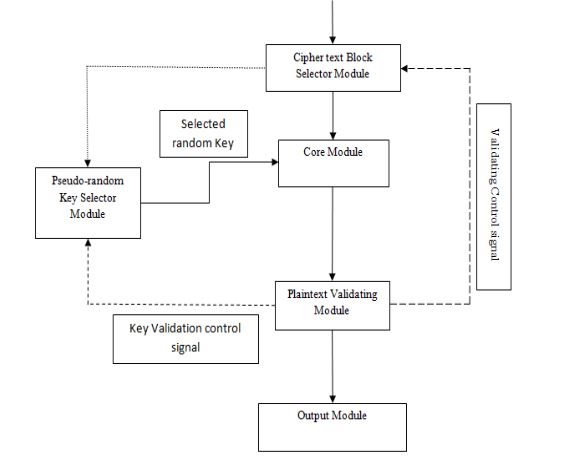
Fig 3. Decryption Module
Decryption process is shown in Fig. 3. Note that an additional processing overhead is introduced when decrypting the first block since the correct key has to be found. Once the first block is decrypted the subsequent blocks are decrypted using keys dictated by the pseudo-random generator.
CONCLUSION AND FUTURE WORK
This work proposes DP based communication model which incorporates MKE scheme for security purpose improves the performance of wireless networks. It has reduced the energy consumption costs for the data transmission as well as processing cost by 65% and practically doubled the network lifetime. Also, it reduced the energy inequalities among the network thus improving utilization of the network resources.
Additionally, the communication cost in terms of delay is reduced since fewer bits have been transmitted. Consequently, the communication bottlenecks have lesser effect on the quality of service. The proposed scheme incorporates MKE security scheme that reduces the overhead caused due to security implementation in terms of energy consumed and process delay, which are often neglected in existing security implementations for wireless networks.
This work proposes MKE scheme by improving the way the AES algorithm is utilized on links. As a result the MKE improved resilience against a CPA attack while minimizing power consumption. Additionally, it also improves security of AES against brute-force attacks. MKE scheme thwarts CPA attack by reducing correlation between power consumption and the key. The proposed scheme, using 5 keys can decrease the correlation by 80% between power and data.
Also, the energy consumption of the proposed MKE scheme reduces by over 70% when compared to the in homogeneous S-boxes scheme while maintaining high security. Discussed at network level, compromising single key would only compromise a fraction of message thus increasing security against brute-force attacks. Consequently, all the keys have to be compromised before the link becomes unsecure. MKE scheme in network implementation is able to improve resilience of the network against node capture compared to existing schemes.
MKE scheme is analyzed analytically such that time to compromise or number of plain texts required to achieve confidence level of the attacker can be found. This enables the user to periodically update the keys such that nodes can be secured from the attacks. It is also able to improve energy efficiency of the network compared to existing schemes, which makes the network to sustain for longer life periods. Hence the proposed work improves the energy efficiency and performance of the wireless networks while ensuring high data security.
Source: Missouri University
Author: Sandeep Kolli
>> More Wireless Sensor Networks Projects Abstract for Engineering Students
>> More Wireless Energy Projects for Final Year Students