ABSTRACT
This paper presents the Trust Level Routing (TLR) protocol, an extension of the optimized energy-delay routing (OEDR) protocol, focusing on the integrity, reliability and survivability of the wireless network. TLR is similar to OEDR in that they both are link state routing protocols that run in a proactive mode and adopt the concept of multi-point relay (MPR) nodes.
However, TLR aims at incorporating trust levels into routing by frequently changing the MPR nodes as well as authenticating the source node and contents of control packets. TLR calculates the link costs based on a composite metric (delay incurred, energy available at the neighbor node, energy spent during transmission and the number of packets sent on each link) for the selection of MPR nodes.
We highlight the vulnerabilities in OEDR and show ways to counter the possible attacks by using authentication and traffic partition as a basis for mitigating the effects of malicious activity. Network simulator NS2 results show that TLR delivers the packets with a noticeable decrease in the average end-to-end delay with a small increase in the power consumed due to the additional computational overhead attributed to the security extension.
SECURITY THREATS
A major focus is the security of the ad hoc network where the integrity of data is essential. Due to the absence of a central authority for authentication, simple network functions, such as packet forwarding, become susceptible to attacks as they are executed by the nodes on the network instead of trusted centralized routers.
TRUST LEVEL ROUTING
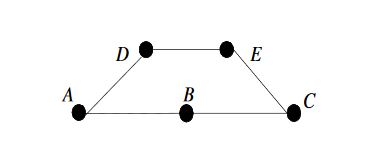
Figure 1: A simple ad hoc network consisting of 5 nodes
For this metric, the best path is selected based on the least consumed total energy. It is worth mentioning that a trade off between the two metrics exists. For example, in the network shown in Figure 1, assuming that the energy consumed per each link is equal, and that node B is heavily congested.
TLR IMPLEMENTATION
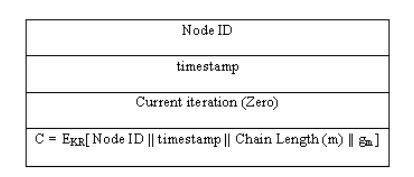
Figure 2: Chain tip packet format
It is worth mentioning that the use of public key cryptography is only applied on the control packets which comprise a smaller part of the whole packets being communicated. The broadcast of the last calculated value in the chain gm is done using a new packet called the Chain Tip packet. The format of the packet is shown in Figure 2.
SECURITY ANALYSIS OF TLR
An adversary may hold old copies of TC packets to transmit them at a later instance of time. This would result in conflicting information in the routing tables since either the topology or the MPR nodes would have changed. TLR mitigates this threat with the use of a timestamp in packets which is further enforced by the hash chain.
OPTIMALITY ANALYSIS OF TLR
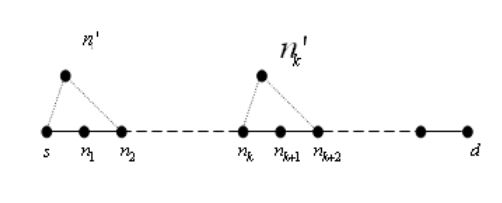
Figure 4: Case III
Case III: There is a trusted optimal path from source to destination such that all the intermediate nodes on the path are selected as MPRs by their previous nodes on the same path.
SIMULATION RESULTS
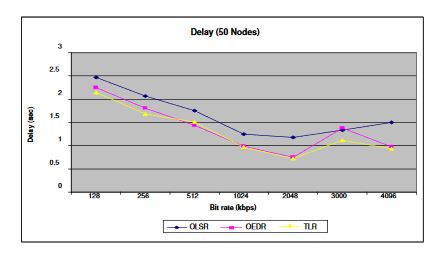
Figure 5: Delay for the three routing protocols in a 50 node network
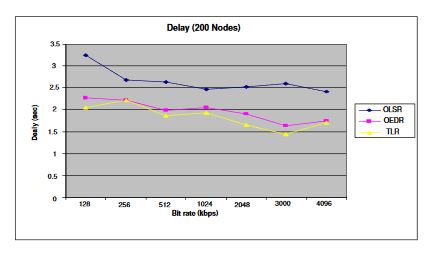
Figure 6: Delay for the three routing protocols in a 200 node network
Figure 5 and Figure 6 display the average end-to-end delay for data packets on networks of 50 and 200 nodes, respectively. The delay in TLR is similar to that of OEDR. In some cases, however, it is less and that is due to the implicit congestion avoidance in TLR. When a sequence of packets is sent through a path, the congestion in the intermediate nodes will increase. Since TLR sends data through different paths, it avoids causing congestion in the intermediate nodes, thus reducing the average delay.
CONCLUSIONS
With the rapid deployment of wireless networks, security of the routing protocols is essential for reliable operation. The threats presented in this paper indicate that more work is needed to guarantee the privacy and integrity of the data. This is especially important in military and safety critical environments. TLR, an extension of the OEDR protocol, resulted in better management of route selection for security purposes.
The simulation results indicate that TLR delivered the packets with a noticeable decrease in the average end-to-end delay. This, however, increased the power consumed when longer routes were selected. The addition of the authentication model in NS2 demonstrated how the TLR protocol dropped non-authentic control packets. Nevertheless, more work needs to be done to improve the model to enable the analysis of the computational overhead involved in computing the hash fields as well as the bandwidth utilized for the additional bytes inserted into the control packet in the form of the hash code.
Source: Missouri University
Authors: Eyad Taqieddin | Ann K. Miller | Jagannathan Sarangapani
>> More Wireless Energy Projects for Final Year Students
>> More Wireless Projects Implementation in Ns2 for Engineering Students