ABSTRACT
This dissertation studies three independent research topics in the general field of wireless communications.The first topic focuses on new receiver design with low-resolution analog-to-digital converters (ADC). In future massive multiple-input-multiple-output (MIMO) systems, multiple high-speed high-resolution ADCs will become a bottleneck for practical applications because of the hardware complexity and power consumption. One solution to this problem is to adopt low-cost low-precision ADCs instead.
In Chapter II, MU-MIMO-OFDM systems only equipped with low-precision ADCs are considered. A new turbo receiver structure is proposed to improve the overall system performance. Meanwhile, ultra-low-cost communication devices can enable massive deployment of disposable wireless relays. In Chapter III, the feasibility of using a one-bit relay cluster to help a power-constrained transmitter for distant communication is investigated. Nonlinear estimators are applied to enable effective decoding.
The second topic focuses prototyping and verification of a LTE and WiFi co-existence system, where the operation of LTE in unlicensed spectrum (LTE-U) is discussed. LTE-U extends the benefits of LTE and LTE Advanced to unlicensed spectrum, enabling mobile operators to offload data traffic onto unlicensed frequencies more efficiently and effectively. With LTE-U, operators can offer consumers a more robust and seamless mobile broadband experience with better coverage and higher download speeds. As the coexistence leads to considerable performance instability of both LTE and WiFi transmissions, the LTE and WiFi receivers with MIMO interference canceller are designed and prototyped to support the coexistence in Chapter IV.
The third topic focuses on theoretical analysis of physical-layer secrecy with finite block length. Unlike upper layer security approaches, the physical-layer communication security can guarantee information-theoretic secrecy. Current studies on the physical-layer secrecy are all based on infinite block length. Nevertheless, these asymptotic studies are unrealistic and the finite block length effect is crucial for practical secrecy communication. In Chapter V, a practical analysis of secure lattice codes is provided.
UPLINK MU-MIMO-OFDM RECEIVERS WITH LOW-RESOLUTION ADCS
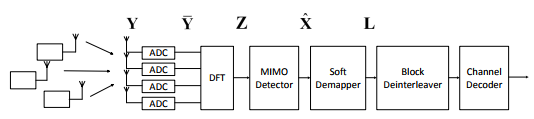
Figure 1: Conventional receiver structure for the MU-MIMO-OFDM system
In the conventional receiver design, the quantization error is approximated as a Gaussian noise and spread more or less uniformly over the Nyquist bandwidth. The underlying assumption is that the quantization error is uncorrelated to the input analog signal, which is accurate enough when high-resolution ADCs are used. In this case, the quantization error can be treated as a channel noise so that it can adopt the conventional receiver structure shown in Figure1.
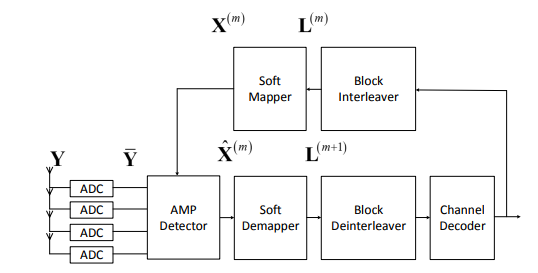
Figure 3: Turbo AMP receiver for dequantization
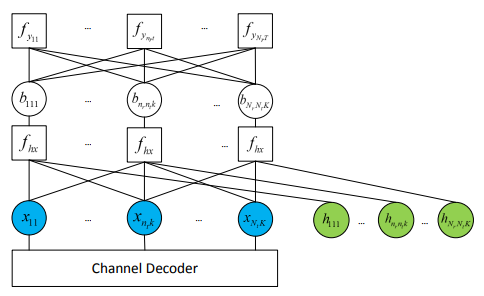
Figure 4: Factor graph for the AMP detector
Belief propagation (BP) is an iterative message-passing type estimator. To reduce the complexity of the turbo receiver, it can adopt approximate-message-passing (AMP) as an alternative signal detector. Figure3 shows the AMP receiver structure. Instead of vector estimations, the AMP detector works on a decoupled-scalars factor graph. For the AMP detector design, it uses the factor graph shown in Figure 4, in which the square and circle represents the factor node and variable node, respectively. The messages are passed between the factor nodes and variable nodes.
ONE-BIT TRANSCEIVER CLUSTER FOR RELAY TRANSMISSION
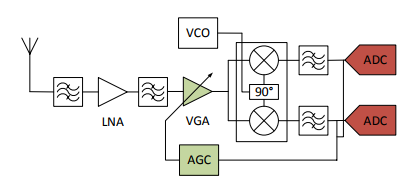
Figure 12: Direct-conversion receiver architecture
Figure 12 shows the architecture of conventional direct-conversion receivers, where a fundamental component is the analog to digital converter (ADC), converting the received signal into digital format with a typical precision of 8-12 bits. For example, a complete direct-conversion receiver RF front end in consists of a frequency synthesizer, a quadrature demodulator (including a Variable Gain Amplifier (VGA) and an Automatic Gain Control (AGC)) and a 10-Bit ADC.
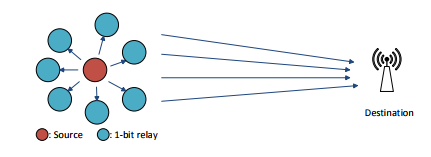
Figure 13: One-bit relays cluster transmission
In this chapter, the feasibility of deploying a one-bit relay cluster for a distant transmission is explored. The envisioned system model is shown in Figure 13, where there are one source node, one destination node and multiple one-bit relays, all equipped with single-antenna. It must be emphasized that the one-bit relays transmit simultaneously at the same frequency band, which completely eliminates the traditional multiple access requirement and thus greatly simplifies the transmission protocol (especially for a large number of relays).
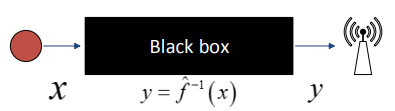
Figure 17: Black box view of the system
Therefore, to solve this problem, instead of using the traditional system model in (1), the destination node will treat the equivalent channel y = ˆf −1 (x) between the source and the destination as a black box shown in Figure 17, and try to find out the relationship between x and y through training data. With the black-box assumption, decoding in the destination node is independent of the number of the relays. In other words, increasing the number of the relays doesn’t increase the system complexity, and failure of multiple the relays has little impact on decoding process.
MIMO INTERFERENCE CANCELLATION FOR LTE AND WIFI COEXISTENCE
Different from burst transmission, the major synchronization of LTE is only required when a user first time accesses the network. The frame synchronization (i.e., MAC layer synchronization) is based on the SSS. The symbol time and frequency synchronization (i.e., PHY synchronization) of LTE users rely on the CPs of OFDM symbols. The PSS can also be used to help time synchronization. The length and position of the CPs vary from different bandwidths. Figure 23 shows the CP length in a slot of different bandwidths.
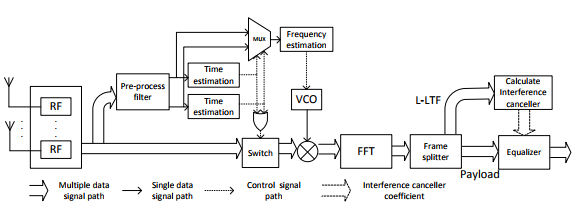
Figure 25: WiFi interference cancelling receiver
The designed WiFi receiver structure is demonstrated in Figure 25. The preprocess filter separate the multiple signal paths from different antennas into two signal paths v1 and v2 based on the method in section C.3. The time estimation method introduced in section B.1 is conducted on both v1 and v2, respectively. The time estimation block will generate a pulse if the correlation value is greater than the threshold. The MUX selects v1 or v2 based on the result of the time estimation block. Then the frequency estimation will be conducted on the signal path selected by the MUX.
The frequency estimation result drives a VCO to generate a sine waveform to compensate the frequency offset on the signal path. For burst transmission, the pulse generated by the time estimation block will turn on a switch at the signal path. The switch will be turned off after reading the whole packet based on the length information in the L-SIG. After the time and frequency synchronization, the signals are converted into frequency domain by FFT. The frame splitter picks the L-LTF signal, and the interference canceller is obtained based on the L-LTF.
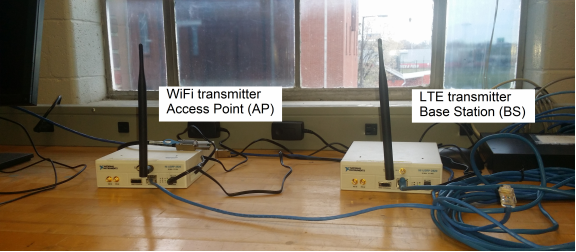
Figure 28: Transmitter location
In the current stage, the sampled data from USRP N210 is processed off-line. The benefit of the off-line receiver is easier to measure the performance quantitatively. Furthermore, it is more convenient to take the advantage of GUI software such as MATLAB to demonstrate performance. For the next stage of prototyping, we will realize the real-time receiver with GNU-Radio. Two USRP N210 are used to implement a two-antenna WiFi or LTE receiver.
The WiFi transmitter (i.e., AP) and LTE transmitter (i.e., BS) is realized by only one USRP N210 each. The transmitted signal waveform is generated from 801.11 and LTE PHY standards. The test scenario is the 2nd floor of W.S. Speed Hall, University of Louisville. Both the WiFi and LTE transmitters are placed at location (A) as shown in Figure 28.
FINITE-BLOCKLENGTH SECRECY PERFORMANCE OF LATTICE CODES
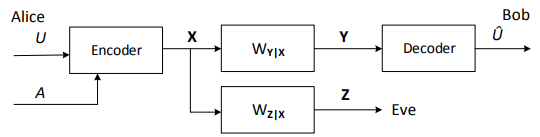
Figure 34: Wiretap channel model
The theoretical foundation of the physical-layer security can be traced back to the early works of Wyner, Csiszar and Korner. In, Wyner introduced the notion of the wiretap channel, which was further generalized by Csiszar and Korner. The wiretap channel model is shown in Figure34, where there are two legitimate communicators: Alice and Bob. Alice wishes to send a secret message U, u ∈ {1, 2 · · · , M0}, to Bob through the main channel X,Wy|x,Y.
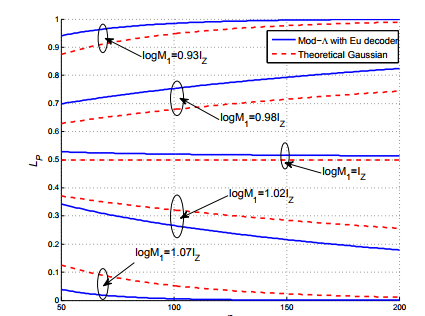
Figure 42: Leak probability Lp vs blocklength n, Comparison of the Mod-Λ Euclidean decoder and the blocklength-n Gaussian channel.
Assume Eve adopts the Mod-Λ Euclidean decoder with a received SNR of 10dB, evaluate LP and compared it with the result of the blocklength-n Gaussian channel in Section III. Figure 42 shows Lp versus n, when log M1 = 0.93Iz, 0.98Iz, Iz, 1.02Iz and 1.07Iz. From Figure 42, it gives the following observation. For the secure lattice codes with finite blocklengths, Lp is below the theoretical value when log M1 is greater than the channel capacity, and Lp will be greater than its theoretical value when log M1 becomes smaller than the channel capacity.
CONCLUSION
In this Chapter, a practical approach to analyze secure lattice codes with finite blocklengths was provided. The idea to find computationally trackable analysis is to utilize the second-order. The idea and technique presented can be applied to various scenarios for the analysis of the finite blocklength secrecy. For a specific code design, it is necessary to analyze its trade-off between the reliability and the secrecy.
Source: University of Louisville
Author: Chen Cao
>> 60+ Antenna Communication Projects for Engineering Students
>> Antenna Projects using Matlab Code for Engineering Students
>> Projects on Microstrip Antenna and Wave Propagation for Engineering Students
>> More Matlab Projects on Signals and Systems for Students
>> 200+ Matlab Projects based on Control System for Final Year Students