ABSTRACT
Due to the explosive growth of mobile data traffic and the shortage of spectral resources, 5G networks are envisioned to have a densified heterogeneous network (HetNet) architecture, combining multiple radio access technologies (multi-RATs) into a single holistic network. The co-existing of multitier architectures bring new challenges, especially on resource management and security provisioning, due to the lack of common interface and consistent policy across HetNets. In this thesis, we aim to address the technical challenges of data traffic management, coordinated spectrum sharing and security provisioning in 5G HetNets through the introduction of a programmable management platform based on Software-defined networking (SDN).
To address the spectrum shortage problem in cellular networks, cellular data traffic is efficiently off loaded to the Wi-Fi network, and the quality of service of user applications is guaranteed with the proposed delay tolerance based partial data off loading algorithm. A two-layered information collection is also applied to best load balancing decision-making. Numerical results show that the proposed schemes exploit an SDN controller’s global view of the HetNets and take optimized resource allocation decisions. To support growing vehicle-generated data traffic in 5G-vehicle adhoc networks (VANET), SDN-enabled adaptive vehicle clustering algorithm is proposed based on the real-time road traffic condition collected from HetNet infrastructure. Traffic off loading is achieved within each cluster and dynamic beamformed transmission is also applied to improve trunk link communication quality.
To further achieve a coordinated spectrum sharing across HetNets, an SDN enabled or- chestrated spectrum sharing scheme that integrates participating HetNets into an amalgamated network through a common configuration interface and real-time information exchange is proposed. In order to effectively protect incumbent users, a real-time 3D interference map is developed to guide the spectrum access based on the SDN global view. MATLAB simulations confirm that average interference at incumbents is reduced as well as the average number of denied access.
Moreover, to tackle the contradiction between more stringent latency requirement of 5G and the potential delay induced by frequent authentications in 5G small cells and HetNets, an SDN-enabled fast authentication scheme is proposed in this thesis to simplify authentication handover, through sharing of user-dependent secure context information (SCI) among related access points. The proposed SCI is a weighted combination of user-specific attributes, which provides unique fingerprint of the specific device without additional hardware and computation cost. Numerical results show that the proposed non-cryptographic authentication scheme achieves comparable security with traditional cryptographic algorithms, while reduces authentication complexity and latency especially when network load is high.
ENABLING TECHNOLOGIES AND CHALLENGES OF 5G HETNETS
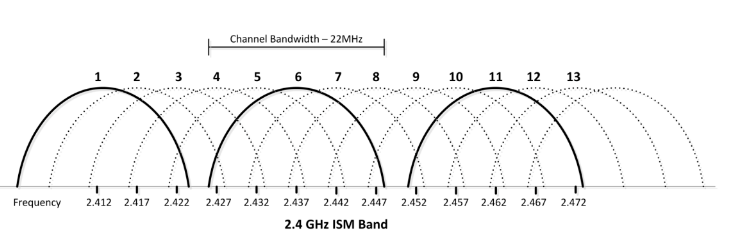
Figure 2.1: IEEE 802.11b / g channels; 1, 6, and 11 are three orthogonal channels
During the signal transmission, a Wi-Fi signal occupies five sub-channels in the 2.4 GHz frequency band. Any two sub-channels that differ by five or more in the numbers, such as 3 and 8, do not overlap with each other. For example, channels 1, 6, and 11 are the only non- overlapping channels, as shown in Fig.2.1. Channels 1, 6, and 11 are the only group of three non-overlapping channels in North America and the United Kingdom. In Europe and Japan using Channels 1, 5, 9, and 13 for 802.11g and 802.11n is recommended.
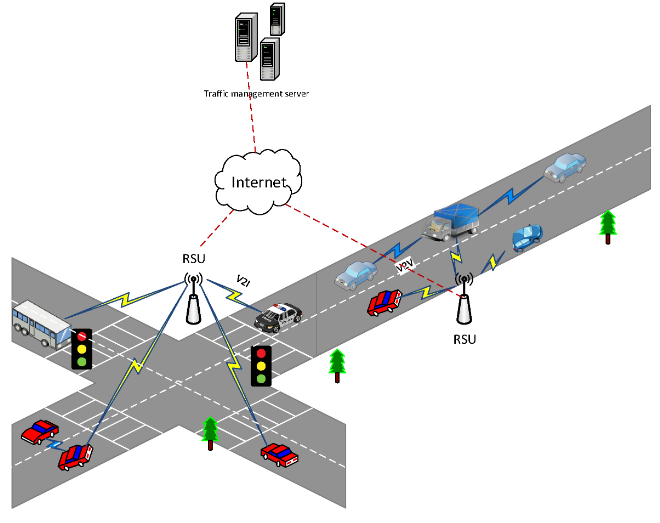
As shown in the Figure 2.2 above, VANET architecture mostly includes vehicles moving on the road that are embedded onboard units, RSUs and a server (e.g., traffic management server) that are in charge of the resource allocation of the distribute RSUs. RSUs serve as the gateway between vehicle networks and other networks or agents, such as the Internet and the remote control server. It can also be seen from the figure that there are two types of links in VANET: vehicle-to-vehicle (V2V) communication and vehicle-to-infrastructure (V2I) communication. For V2V communication, vehicles exchange message with neighbor nodes in an adhoc manner without a high-level coordination. In V2I communication, vehicles share the message with RSUs.
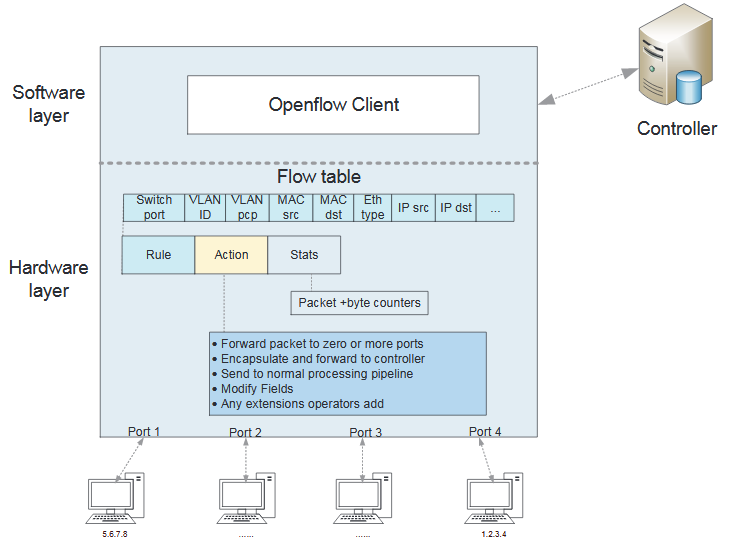
As shown in Fig.2.4 above, flow table includes match fields, rules, and action. The rule defines the flow, which consists of the mainly field in the packet header. Each header field can be a wild-card to allow for aggregation of flows. Identification of link layer, network layer, and transport layer are in match fields. The action defines how the packets should be processed, while Statistics keep track of the number of packets and bytes for each flow, and the time since the last packet matched the flow (to help with the removal of inactive flows).Each flow entry in the flow table of the switch has a simple action associated with it.
For example, forwarding, encapsulating and dropping. Forwarding a flow’s packets to a given port allows packets to be routed through the network according to predefined rules. Encapsulate and forward a packets to the controller mean that a packets, typically the first one in a new flow, is encapsulated and forwarded to the controller through secure channel, so that controller can decide if the flow should be added to the Flow Table. Packets are dropped when there is security consideration, i.e., to curb denial of service attacks, or to reduce spurious broadcast discovery traffic from end-hosts.
SDN-ENABLED DATA OFF LOADING AND LOAD BALANCING IN 5G HETNETS
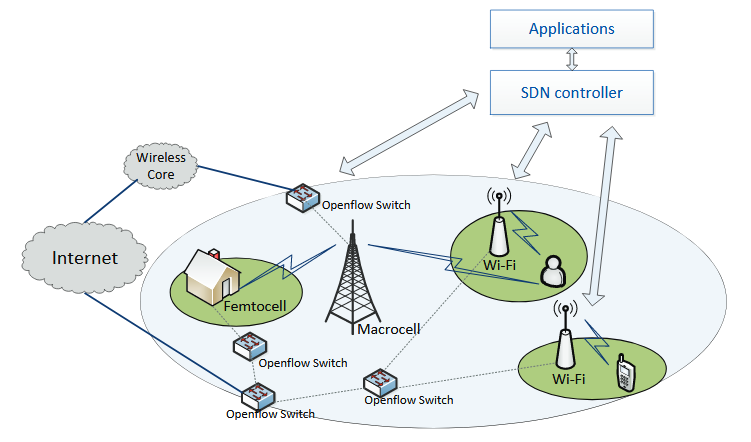
Figure 3.1: SDN-based wireless heterogeneous network structure with control plane design
In this section, we present SDN-based traffic management algorithms for the heterogeneous network shown in Figure 3.1. To this end, we attempt to alleviate spectrum shortage and network congestion in the cellular network by using SDN-enabled mobile data off loading and load balancing. More specifically, to address the shortage of spectrum, data from the cellular network is off loaded onto a Wi-Fi network whenever the cellular users move within the Wi- Fi range.
On the other hand, to deal with network congestion, load balancing is utilized to distribute traffic across multiple cells evenly. For both these cases, all of the decision makings is accomplished by the centralized SDN controller. As mentioned previously, the introduction of SDN facilitates efficient coordination between the cellular and Wi-Fi networks. Moreover, the performance of load balancing can also be improved significantly by exploiting the controller’s view of the whole network. In the next subsection, we present an SDN-based data off loading algorithm.
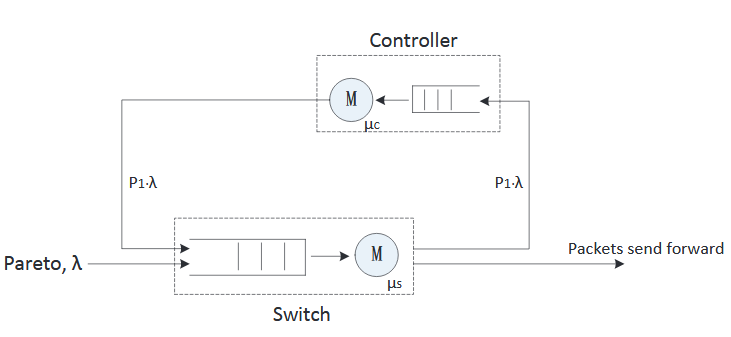
Figure 3.5: A model for SDN switch and controller
The average delay introduced by SDN depends on the state of the flow table within the switch, i.e., whether or not the switch’s flow table contains a rule for the incoming traffic flow. Figure 3.5 shows the queuing model for the controller and the switch.
In Figure 3.5, λ is the data arrival rate while μs and μc represent the processing rates at the switch and the controller, respectively. As shown in the figure, if the packet arriving at the switch is the first packet of a new data flow (new source-destination pair), the switch forwards this packet to the controller. The controller decides the optimal forwarding rule for this packet and returns it to the switch.
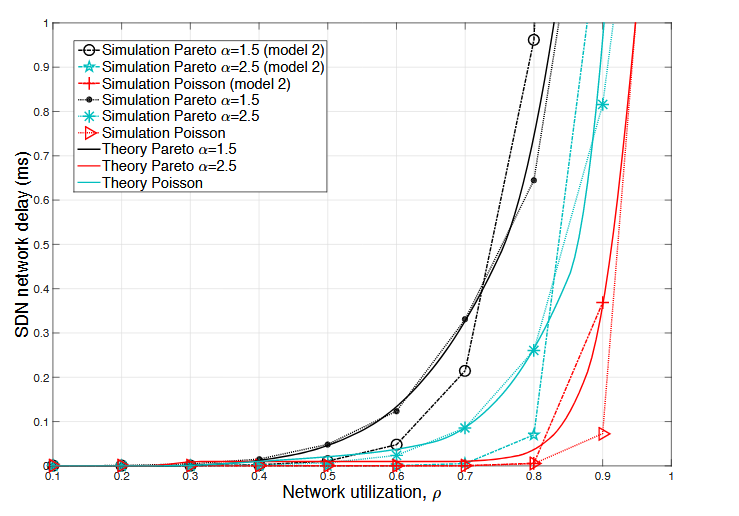
Figure 3.6: SDN network delay versus network utilization using different SDN queuing model
Figure 3.6 shows the SDN delay as a function of the network utilization ρ. Recall that in the queuing model introduced in Section 3.4.1, it was assumed that the packets returning from the controller to the switch cause negligible delay in the switch queue. To justify this assumption, in Figure 3.6, we also plot the SDN delay which occurs when the effect of the packets returning from the controller is not ignored (Model 2 in Figure 3.6).
From the figure, it can be seen that the simulation results with and without the aforementioned assumption follow approximately the same trend and therefore, our assumption is justified. Moreover, it can also be seen that the theoretical and the simulation results also match very closely with each other, thus verifying the validity of the SDN processing delay analysis in Section 3.4.1.
SDN-ENABLED TRAFFIC OFF LOADING AND BEAM FORMED TRANSMISSION IN 5G-VANET
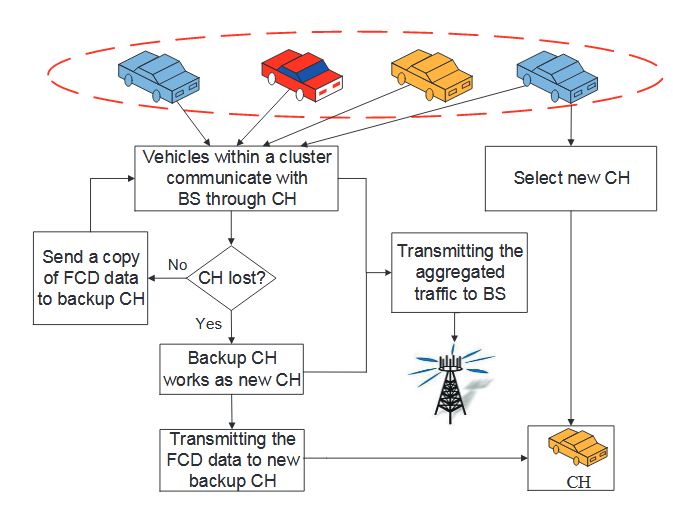
Figure 4.3: The dual cluster head selection scheme
In this dual CH scheme, a backup CH is also selected according to the CH selection criteria. The existing CH always sends a copy of FCD data to the back-up CH, as shown in Fig.4.3. Once there is something wrong with the CH, such as an accident or unpredictable emergencies, backup CH would be well prepared and thus is able to take over the responsibility seamlessly.
Moreover, the backup CH also works as a smooth transition during handover procedure to a new CH. This is to say, under the scenario that the existing CH leaves cluster normally, backup CH becomes CH immediately and a new back-up CH would be selected, as we can see in Fig.4.3. The dual CH design is especially beneficial for 5G latency-stringent application with reduced communication interruption probability.
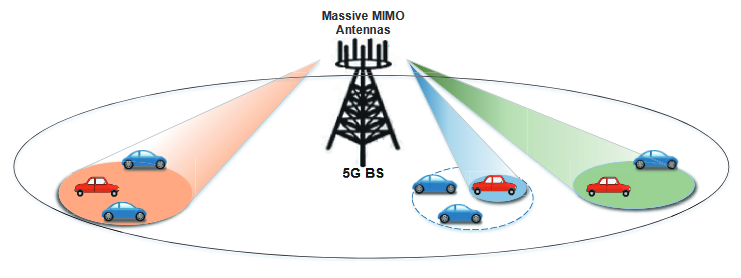
Figure 4.4: The beamforming design and directional coverage cover the vehicle clusters along a road crossing the cell
The two beamforming solutions are shown in the right part of Fig.4.4 further provide flexibility and adaptivity for the beamforming design of SDN-enabled 5G-VANET. In the first solution, the beam only covers the cluster head to optimize the beam width and reduce intra- beam interference. In the second technology, the beam covers the whole cluster. Although a wider beam in the latter scheme is less focused and achieves lower signal to interference and noise ratio (SINR) than a more focused beam, it has the advantage of better coverage and guarantees the seamless connection during CH failure. Therefore, due to the high mobility of vehicles, it is preferred that wider beam is utilized to enhance coverage in the proposed SDN- enabled 5G-VANET architecture. Furthermore, when there are multiple clusters co-exists and close to each other, the narrow beam will be applied to reduce interference and improve the trunk link throughput rate.
SDN-ENABLED ORCHESTRATED SPECTRUM SHARING IN 5G HETNETS
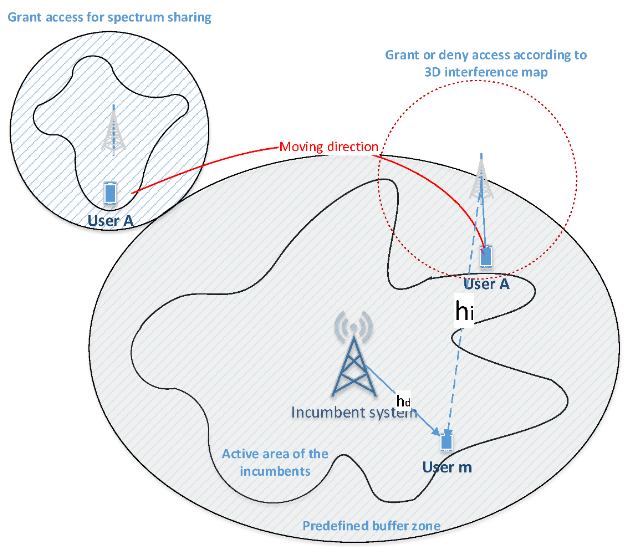
Figure 5.3: The interference map and buffer zone for the protection of existing users during spectrum sharing
Fig.5.3 shows the calculated interference map used during spectrum sharing procedure. As the channel condition varies over space at distributed locations, interference from co-channel transmitters could also be very different during user mobility due to the varying propagation distance, the activity of interfering signals and impact of the surrounding environment. Therefore, it is believed that spectrum could be shared for shorter time scale instead of simple binary decision for the whole communication session.
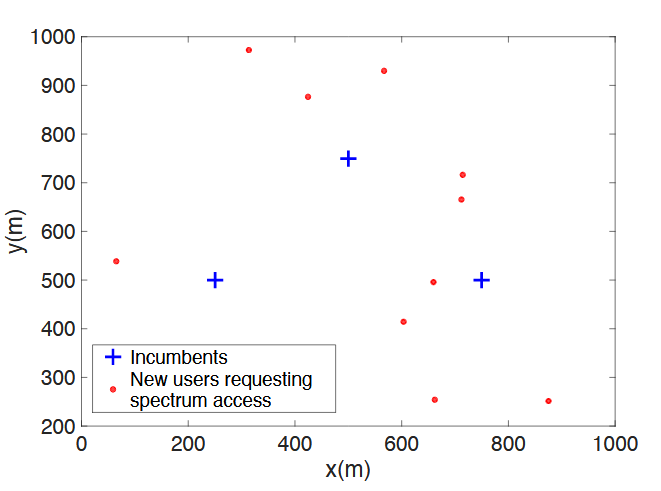
Figure 5.4: Simulation set up of the randomly generated incumbents and new accessing users
Fig.5.4 shows the simulation setup of incumbents and randomly generated new users who are requesting spectrum resources. Assume that three incumbent users were communicating at frequencies of 900 MHz, 3.5 GHz, and 480 MHz. Here 900 MHz is licensed spectrum, while 3.5 GHz and 480 MHz are incumbent spectrum pools for sharing. 3.5 GHz is used as one of the spectra for sharing because Federal Communications Commission (FCC) has engaged in creative frequency allocation and recently adopted rules to allow shared commercial use of 150 MHz of spectrum in the 3550-3700 MHz (3.5 GHz) band, called the Citizens Broadband Radio Service. Hence, 3.5 GHz frequency band is selected as an example to show the performance, and 480 MHz is an example for DTV spectrum.
SDN-ENABLED SECURITY PROVISIONING IN 5G HETNETS
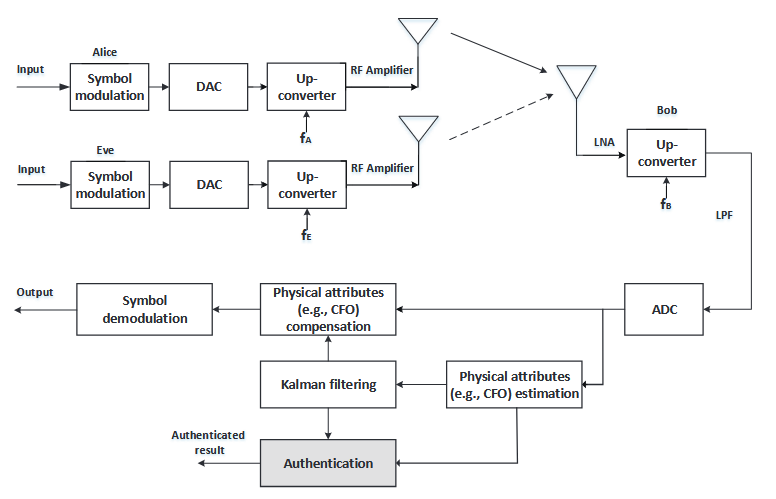
Figure 6.2: SCI based authentication using unique user physical layer attributes associated with each transmitter-and-receiver pair
As shown in Fig.6.2, Alice generates baseband signals, which is then modulated to a carrier frequency fA after digital-to-analog conversion (DAC). The signal is then transmitted and arrived at Bob. The radiated RF signal would then be converted to the baseband. As there are different oscillator characteristics and Doppler shift due to mobility, some physical layer attributes would be unique between Alice and Bob.
For example, the carrier frequency of Alice and Bob would not be the same, resulting in a carrier frequency off set (CFO), i.e., δ fA = fA − fB, while the CFO between Eve and Bob would be δ fE = fE − fB. Due to the manufacture independence of devices, the received signal that is sent from different transmitters would experience distinctive CFOs at the various time instant. Therefore, the unique physical layer attributes such as CFO that are associated with each pair of transmitter and receiver can be used as the identification if combined properly.
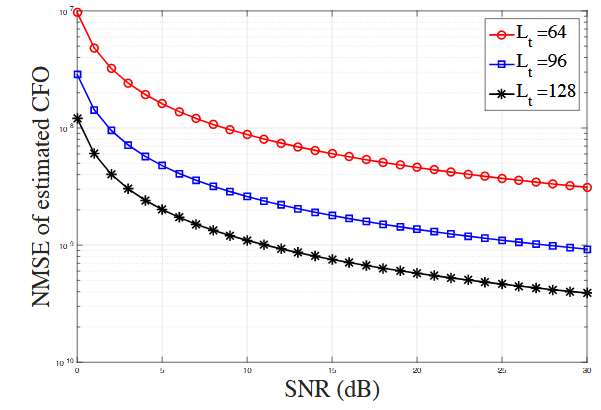
Figure 6.3: NMSE of CFO estimates vs. SNR with different training lengths
Fig.6.3 shows the normalized mean square error (NMSE) of the estimated CFO versus SNR. It can be seen that the estimation error of CFO decreases with the increase of SNR. This is reasonable because estimation would be more accurate with better channel quality. It can also be observed that the estimation error reduced when the length of the training segment increases.
CONCLUSION
5th generation mobile networks (5G), also referred to as beyond 2020 mobile communications systems, represent the next major phase of the mobile telecom industry, going beyond the current Long Term Evolution (LTE) and IMT-advanced systems. In addition to increased peak bit rates, better coverage, and higher spectrum spectral efficiency, 5G systems are required to enable ultra-reliable and low-latency communications (URLLC), support Internet of Things with potential numbers of diverse connectable devices, including massive machine type communications (mMTC) devices. All in all, 5G should be cost-efficient, flexible deployable, elastic, and above all programmable.
To realize the flexible and elastic deployments and cope with the ever growing mobile data traffic, lots of research has been conducted in terms of 5G network management, resource allocation, as well as security provisioning.However, technical challenges still exist due to the complicated communication scenario. This thesis carries out a comprehensive study on 5G techniques which mainly explored the efficient management of heterogeneous networks: the resource management solutions including traffic off loading and spectrum sharing in high load scenario and 5G-VANET, and the security management in heterogeneous small cell deployment.
We developed a number of effective and efficient schemes for these problems through the coordination of SDN platform.The contributions that have been made in this thesis and the conclusions drawn from these contributions can be summarized as follows:In Chapter 3, the novel SDN-based Wi-Fi data off loading and load balancing algorithms were proposed to cope with the increased data traffic and heterogeneous network structure.The new algorithms utilized the controller’s global view of the network to take more informed decisions for efficient resource management. We also analyzed the performance of the proposed algorithms under realistic load conditions.
To this end, we first introduced a queuing model with Pareto arrivals to investigate the processing and forwarding delays incurred due to the SDN architecture.Then, we analyzed the performance of the proposed SDN-based partial data off loading scheme in terms of the threshold miss probability and the amount of data off loaded successfully onto Wi-Fi.Through simulations, it was shown that partial data off loading saves primary resources and decreases threshold miss probability by 20% ∼ 50%, which ultimately improves the application performance at the user end. Furthermore, the simulation results also confirmed that SDN-based LB outperforms the baseline methods by minimizing the number of required handovers by 50% and by balancing the loads more evenly across multiple cells.
Our results and discussions showed that the delay incurred by SDN is well within the acceptable limits for most applications. Particularly, it has been demonstrated that SDN-based solutions perform better for large data traffic with high delay tolerance. All in all, SDN is proved to be a suitable enabling technology for introducing intelligence within the wireless networks and for providing fine-grained control to the network operators.
Source: Western University
Author: Xiaoyu Duan
>> Latest 50+ IoT based Security Projects for Engineering Students
>> Top IoT Projects using Matlab for B.E/B.Tech Students
>> 200+ IoT Led Projects for Final Year Students
>> IoT based Networking Projects for Final Year Students
>> IoT Software Projects for Final Year Students
>> 50+ Matlab projects for Digital Image Processing for Final Year Students
>> More Matlab Projects on Signals and Systems for Students
>> 200+ Matlab Projects based on Control System for Final Year Students