ABSTRACT
Cloud computing brings flexible and cost – effective services. However, security concerns plague the cloud. Data confidentiality is one of the security concerns inhibiting the adoption of cloud computing. This concern stems from various cyber attacks directed towards gaining unauthorized access to cloud – bound or cloud – hosted data. This paper proposes a client – end encryption and key management system to curb cyber attacks that target compromising data confidentiality on the cloud. The proposed system uses chaotic atmospheric noise to generate a fitness function. The fitness function is used to generate random numbers, which are used to create encryption keys. The strength of the encryption keys is derived from the chaotic and random nature of the atmospheric noise.
The keys are then used for encrypting cloud – bound data using Advanced Encryption Standard (AES – 128, 192 and 256 ), Data Encryption Standard (DES), 3 – DES, and our novel cryptosystem named Cryptor, before it can be sent to the cloud. However, encryption bears no significance if the key management system is flawed. To address the inherent key management problem, the solution uses a neural network to learn patterns of an encryption key. Once learnt, the key is discarded to thwart possible key attacks. The key is reconstructed by the neural network for decryption purposes.
LITERATURE REVIEW
Various research related to cloud encryption has been conducted. In the quest to achieve data confidentiality, encryption is cited as the widely – used method.
Neural cryptography is a new technique for providing data confidentiality. This technique combines the concepts of machine learning and cryptography, using neural networks (NNs). Artificial intelligence techniques are proposed to invent cryptosy stems to curb eavesdropping. This research proposes two artificial neural networks for develop a cryptographic algorithm to protect data. The encryption part was a success as the neural networks successfully communicated securely, avoiding eavesdropping.
PROPOSED MODEL SOLUTION
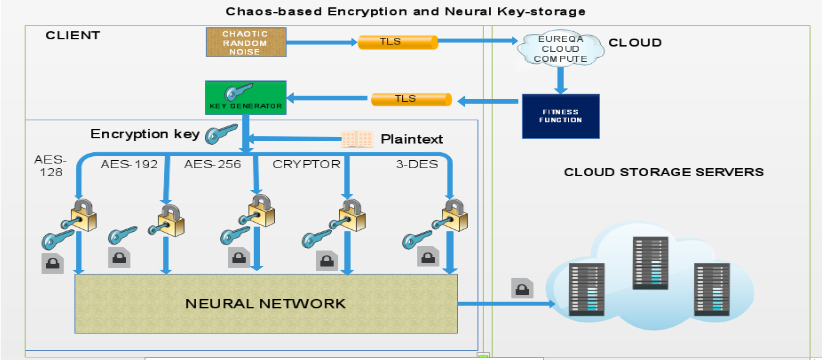
Each of these requirements is taken into consideration in the design and implementation of the proposed model. The proposed model is presented by Fig.1 below which depicts the architecture of the proposed encryption and key management scheme The model describes the process of encrypting cloud – bound data on the client – end and how encryption keys are managed.
The process is initiated by generating random noise. The noise can be from any source. In this paper, the noise was sourced from. The noise is then transmitted into the Eureqa cloud – based system through a secure channel, using transport layer security (TLS). Eureqa implements an exhaustive search which mimics the concepts of evolutionary computing to generate a non – linear fitness function that fits the input noise.
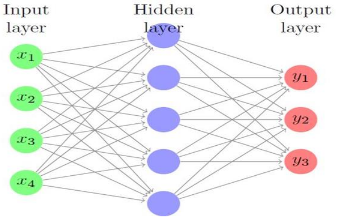
Figure 2 : Structure of a CPNN
A CPNN is a hybrid of other neural networks. It consists of a combination of a structure widely known as a competitive network. A CPNN is a variant of a neural network consisting of three layers: the input, Kohonen (i.e. hidden) and Grossberg (i.e. output) layers. The structure of a CPNN is depicted in the fig. 2.
There are two important aspects of a CPNN. These are supervised and unsupervised learning. The Grossberg layer uses supervised learning while the Kohonen layer uses unsupervised learning. Depending on the learning scheme used, the weights of the input vectors are automatically changed. The inputs to the CPNN are the encryption key and the ciphertext, as a set of vectors, in binary form. Given a set of vector pairs ( X1 , Y1 ), ( X2 , Y2 ),…, ( Xm, Ym ), a CPNN is able to learn and associate an X vector given in the input layer with a Y vector.
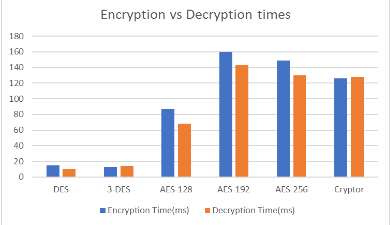
Figure 3 : Encryption vs Decryption time
Fig. 3 depicts the encryption and decryption times, measured in milliseconds for all five encryption schemes.Cryptor took 126 milliseconds to encrypt the text file. DES encrypted the text file in 12 milliseconds. 3 – DES encrypted the text file in 13 milliseconds. AES – 128 took 87 milliseconds, AES – 192 took 160 milliseconds and AES – 256 recorded 149 milliseconds to encrypt the same text file.
CONCLUSION
This paper presented a novel cryptographic scheme based on chaos and neural cryptography. The proposed scheme uses chaotic random noise to improve the strength of encryption keys. The strength of the encryption keys does not rely on the length of the key but the random and chaotic nature of the input noise. Several experiments were conducted to test different aspects of the solution implemented. Overall, it is concluded, based on the results, that chaos theory can be applied in cryptography to improve the strength of ciphers.
The result show that Cryptor is a lightweight, strong client – end encryption scheme. Hence, Cryptor is a better encryption scheme in terms of encryption and decryption times. The chaos – based encryption keys can be used to improve the strength of existing cryptosystems such as DES, 3 – DES and AES. Future perspectives include: experimenting on encrypting multi – media digital content, implementing the Cryptor system to have rounds of encryption to increase layers of security, and to test the proposed neural key store against various types of key attacks.
Source: Dublin Institute of Technology
Authors: N.N Mosola | M.T Dlamini | Jonathan Blackledge | J.H.P Eloff | H.S Venter
>> Latest 50+ IoT based Security Projects for Engineering Students
>> IoT based Big Data and Cloud Computing Projects for B.E/B.Tech Students
>> 200+ IoT Led Projects for Final Year Students