ABSTRACT:
Ericsson develops and builds mobile telecommunication networks. These networks consists of a large number of equipment. Each telecommunication company has a staff of administrators appointed to manage respective networks.
In this thesis, we investigate the requirements for an access control model to manage the large number of permissions and equipment in telecommunication networks. Moreover, we show that the existing models do not satisfy the identified requirements. Therefore, we propose a novel RBAC model which is adapted for these conditions.
We also investigate some of the most common used commercial tools for administrating RBAC, and evaluate their effectiveness in coping with our new proposed model. However, we find the existing tools limited, and thereby design and partly implement a RBAC managing system which is better suited to the requirements posed by our new model.
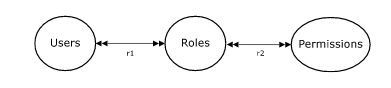
ROLE BASED ACCESS CONTROL (RBAC)
Background:
Traditionally, user access has often been granted by adding permissions per object. In large or complex organizations, users might have to be granted a large number of permissions in order to perform their work tasks.
This becomes even more complex when users are spread over a large number of computers and perhaps over a number of locations. As a consequence of the complexity, it may become hard to determine which users have rights to do what. Administration of users and their permissions can quickly become hard to manage.
Why is RBAC is Needed?
RBAC has been proposed by many authors as an alternative to traditional access control to simplify administration. In large systems, the amount of permissions assigned to a user may become high. It may become hard to keep track of all permissions. When a user moves between positions in the company, her permissions are changed according to her new tasks because administrators do not have a clear view over the users permissions. They may fail to revoke all permissions that are not longer needed.
Enterprise RBAC (ERBAC):
ERBAC, or enterprise RBAC, is an extension of hierarchal RBAC. Large enterprises have systems of many various kinds, e.g Windows, Unix and web applications. ERBAC is developed to provide entire enterprises with RBAC. Kern presents ERBAC.
The OM-AM Concept:
Sandhu has proposed a reference framework for access control design called OM-AM (Objective Model- Architecture Mechanisms), which consist of four abstraction layers: objective, model, architecture and mechanisms. However, the framework, is not limited to access control. For instance security solutions for the music industry[37] have been described with OM-AM.
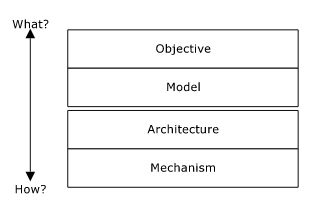
The OM-AM Framework from , Objective and Model Describe What to Be Done, While Architecture and Mechanisms Describe How to Do It.
TARGET ENVIRONMENT
This chapter describes the intended target environment, operation and maintenance networks in telecommunications networks. Some introduction to the WCDMA network is also given.
WCDMA and GSM Networks:
Recent years telecommunications operators have begun to deploy Wide-band Code Division Multiple Access (WCDMA). In networks for mobile telephony and data transfers WCDMA is one of several ”3G” technologies. 2G (GSM) and 3G has similar network topologies. This section describe a simplified view of the WCDMA network but most of it applies to GSM as well.
Operations and Maintenance:
The operations and maintenance network is used by administrators to configure and operate the radio network. Administrative functionality is provided by command line interfaces and various graphical interfaces. An operator can access a network element directly or via the Operations Support System for Radio and Core (OSS-RC). It supports centralized operation and maintenance of both core network and WCDMA as well as other radio networks, including GSM.
Infrastructure:
Application servers and the OSS-RC master server provide operators with functionality. A certificate authority and a single login server are present to secure the solution by providing authentication of hosts and applications and authorization of hosts, users and applications. Certificates and asymmetric keys are used in this process.
RBAC FOR O&M NETWORKS:
A model for management of the network described in chapter 3 is needed. This chapter presents an analysis of requirements on such model and how a model that fulfills them would look like. At the end of the chapter a suitable model is presented.
Methodology:
In order to get to a suitable access control model for the target environment we have taken these steps:
- A set of requirements, or objectives, is constructed by studying the
target environment through various documents. - Existing models are evaluated with respect to these requirements. The result is that none is suitable, therefore new models are created.
- Two new models are created in an attempt to fulfill the requirements.
- Models are evaluated to find the best solution among them.
Objective:
Several requirements need to be fulfilled in order to create a suitable access model for O&M networks. These requirements were identified by studying the available documentation regarding the operation and maintenance environment.
Shortcomings of existing models:
At first a couple of existing access models, e.g ARBAC and ERBAC, seem to fulfill the requirements above. However, this section points out some shortcomings with these models when applied to the target environment. Available models are based on NIST RBAC, Users are assigned to permissions through their role assignments.
EVALUATION OF ADMINISTRATIVE TOOLS
Given the model B, proposed in the previous chapter, the question arises how it can be administered and implemented in the target environment. Concrete questions are:
- Which tools for RBAC are available on the market?
- Are the available tools suitable for the proposed model within the target environment?
This chapter investigates these questions by first establishing a list of criteria for tool evaluation and then examines a selection of available tools with respect to the formulated criteria.
CONCLUSIONS
This thesis was to find a suitable role based access control model for operations and maintenance networks in telecommunications networks. Requirements of such model have been constructed and a suitable model which fulfill them have been presented. Requirements for a tool for administration of the proposed access control model have been constructed. A short market survey have come up with two candidates which have been evaluated. This evaluation shows that neither of them are suitable without extensive modification.
Source: Linkopings University
Author: Peter Gunnarsson