ABSTRACT
The physical security strategy in the wireless network with a single-antenna eavesdropper is studied. The information transmits from a single-antenna source to a single-antenna destination, and an energy-limited multi-antenna relay is employed to forward information. The antennas of the relay are divided into two groups. One group receives and forwards information, and the other converts the received signal into energy. Beamforming is used by the relay to prevent the eavesdropper from intercepting confidential information.
For the purpose of maximizing the secrecy rate, antenna grouping and beamforming vectors are designed. A low complexity scheme of antenna grouping is presented. The simulation results show that the secrecy rate can be significantly improved by arranging part of the antennas for energy harvesting, and part for forwarding and optimizing the beamforming vector at the relay. The antenna grouping scheme significantly reduces the computational complexity at the cost of acceptable performance loss.
SYSTEM MODEL
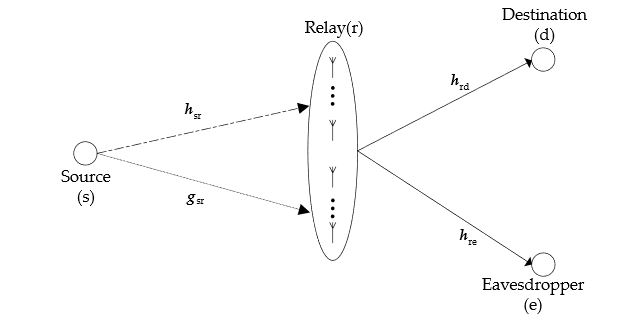
Figure 1. System model
A source (s) transmits information to two receiving nodes, but the information transmitted to one node needs to be kept secret from the other node. Hence, for one receiver, the other receiver is an eavesdropper. Without loss of generality, in a timeslot, the node that receives information is called the destination (d), and the other node is called eavesdropper (e). Since obstacles are present between the source and the receivers, there is no direct link between the source and any receiving node, and, as a result, the information must be forwarded by a relay (r). The system model is shown in Figure 1.
OPTIMIZATION ANALYSIS
As the channels are quasi-static, the channel coefficients over a period of time will be constant. The maximum Rs can be obtained by optimizing four optimization variables: N, Θ, Ω, and w. The first three variables determine the antenna grouping. If the antenna grouping has been determined, i.e., the variables N, Θ and Ω are known, the original optimization problem can be simplified into the optimization of the beamforming vector w.
SIMULATION RESULTS
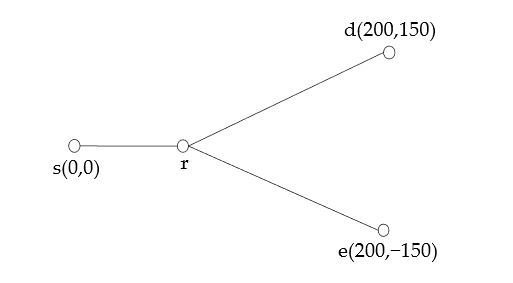
Figure 2. Model used for simulation
The performance of the proposed scheme is simulated in this section. The coordinates of the nodes are shown in Figure 2. We set the source (s), the destination (d) and the eavesdropper (e), respectively, at (0, 0), (200, 150), (200, -150) (Unit: m).
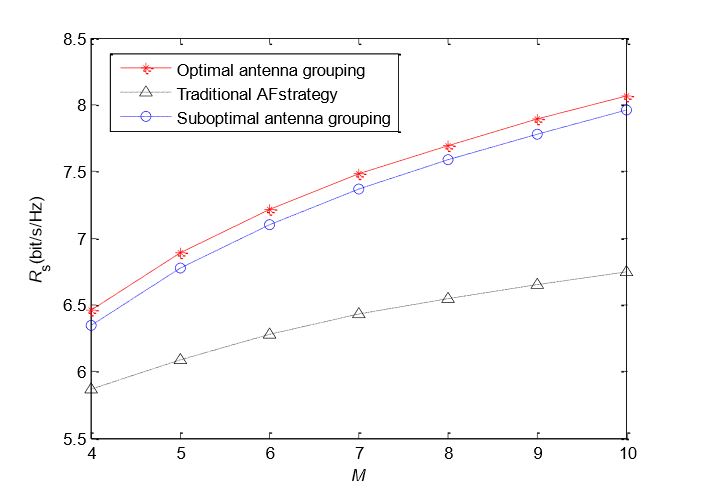
Figure 5. Relationship between antenna number of relay and secrecy rate
The relationship between antenna number of the relay and secrecy rate is shown in Figure 5. We set the coordinate of the relay at (5, 0) and set Ps = 1 mW and P r = 0.01 mW. M increases from four to 10. For the traditional AF strategy, the increase of M will enhance beamforming gain, so the achievable secrecy rate can be improved. However, in the proposed “energy harvesting–AF” strategy, the increase of M has two benefits.
CONCLUSIONS
This paper studies the security transmission in wireless powered relaying systems. In the system model, the source, the destination, and the eavesdropper are respectively equipped with an antenna, and the relay is equipped with multiple antennas to amplify and forward information. The transmission process of confidential information was divided into two stages. In the first stage, the relay converts the received signals in some antennas into energy.
In order to avoid the leakage of information, beamforming is used by the relay when it forwards the information to the destination in the second stage. We divide the antennas of the relay into two groups. The antennas in one group forward the received signals with beamforming, and those in the other convert the received signal to energy for the signal forwarding. We optimize the antenna grouping scheme and beamforming vector to promote the achievable secrecy rate.
Since the overall optimal beamforming vector is difficult to obtain, we use a local optimal beamforming vector. We also propose a low complexity antenna grouping scheme at only the cost of acceptable performance loss. The simulation results show that the proposed “energy harvesting–AF” strategy has better security performance than the traditional AF strategy, especially when the battery power of the relay is low.
Source: Chongqing University
Authors: Weijia Lei | Meihui Zhan
>> Smart Antenna Design Final Year Projects for Engineering Students
>> More Wireless Energy Projects for Final Year Students