ABSTRACT
As embedded computers become ubiquitous, mobile and more integrated in connectivity, user dependence on integrated circuits (ICs) increases massively for hadling security sensitive tasks as well as processing sensitive information. During this process, hardware authentication is important to prevent unauthorized users or devices from gaining access to secret information. An effective method for hardware authentication is by using physical unclonable function (PUF), which is a hardware design that leverages intrinsic unique physical characteristics of an IC, such as propagation delay, for security authentication in real time. However, PUF is vulnerable to modeling attacks, as one can design an algorithm to imitate PUF functionality at the software level given a sufficient set of challenge-response pairs (CRPs).
To address the problem, we employ hardware isolation primitives (e.g., ARM Trust Zone) to protect PUF. The key idea is to physically isolate the system resources that handle security-sensitive information from the regular ones. This technique can be implemented by isolating and strictly controlling any connection between the secure and normal resources. We design and implement a ring oscillator (RO)-based PUF with hardware isolation protection using ARM Trust Zone. Our PUF design heavily limits the number of CRPs a potential attacker has access to. Therefore, the modeling attack cannot be performed accurately enough to guess the response of the PUF to a challenge.
Furthermore, we develop and demonstrate a brand new application for the designed PUF, namely multimedia authentication, which is an integral part of multimedia signal processing in many real-time and security sensitive applications. We show that the PUF-based hardware security approach is capable of accomplishing the authentication for both the hardware device and the multimedia stream while introducing minimum overhead.
Finally, we evaluate the hardware-isolated PUF design using a prototype implementation on a Xilinx system on chip (SoC). Particularly, we conduct functional evaluation (i.e., randomness, uniqueness, and correctness), security analysis against modeling attacks, as well as performance and overhead evaluation (i.e., response time and resource usages). Our experimental results on the real hardware demonstrate the high security and low overhead of the PUF in real time authentication.
BACKGROUND & RELATED WORK
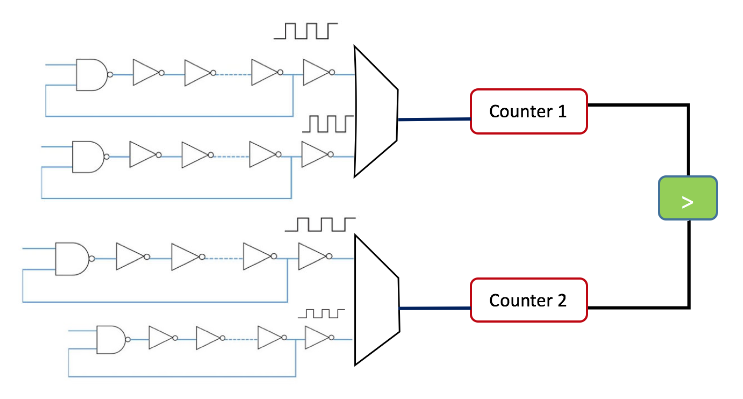
Figure 2.1: Ring Oscillator PUF
Figure 2.1 shows an example of RO PUF. The idea is to make exactly similar paths of ROs and select one of them based on the challenge given to the PUF as input. Then, the selected path will be used as counter clock. Since each path has a unique frequency, the clock works on a unique clock speed and generates the results on a inimitable pace which is leveraged to generate the response based on each challenge. In a RO PUF, all delay loops are identical in theory but, due to the random variations in manufacturing, each loop creates a particular frequency that is slightly different from other loops. Loops are connected to multiplexers where input challenge is being used as selector to connect one input delay loop to a counter.
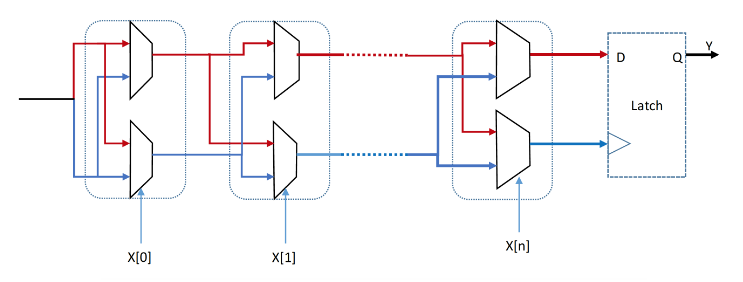
Figure 2.2: Schematic of Arbiter PUF
Arbiter PUF uses delay elements in series, where each element is connected to a multiplexer that chooses a path by using the input challenge. In this scenario, the challenge is being used as multiplexers selectors as it is shown in Figure 2.2. The response of the arbiter PUF depends on which path has the fastest signal propagation. The arbiter performs as a referee to tell which path gets to D flip-flop faster and consequently the fastest path will be connected to output Y. Although the Arbiter PUF is fast, it has two main disadvantages. First, it requires symmetrical routing at each stage, otherwise the unity of responses are not guaranteed. This makes the FPGA implementation difficult. Second, Arbiter PUF is prone to modeling attack.
DESIGN AND IMPLEMENTATION OF RING OSCILLATOR PUF
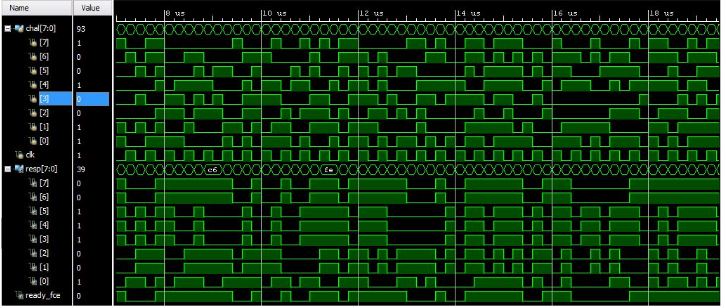
Figure 3.1: Post-Synthesis Timing Simulation
Once a valid clock signal is received by the counter, it starts to count with positive edge of its clock until it overflows (i.e., obtaining all 1’s in the output and restarts again). Based on the unique frequency of each clock, one of the counters overflows sooner than others, which contributes to and generates the response bits. The result of post synthesis implementation using Xilinx Vivado toolchain is shown in Figure 3.1.
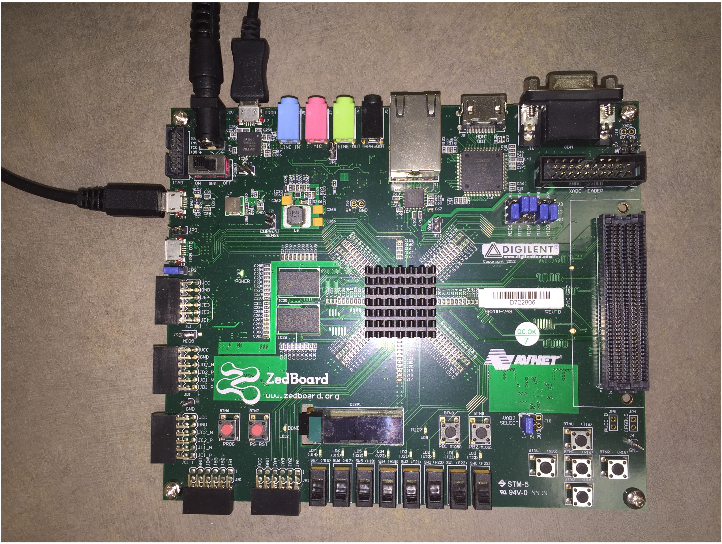
We implement the RO PUF on Xilinx ZedBoard as shown in Figure 3.2, using the Vivado toolchain. The ZedBoard has both programmable logic (PL) and a processing system (PS) with ARM processor. Our PUF design is based on a modified version of the implementation presented.
PROTECTING PUF USING HARDWARE ISOLATION
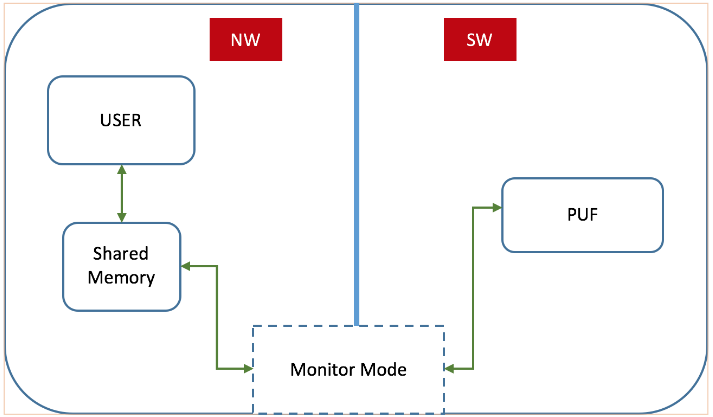
Figure 4.1: Using Trust Zone to Protect PUF
Figure 4.1 shows the overall framework of our hardware isolation-based PUF protection scheme. ARM Trust Zone divides the application runtime into a normal world (NW) and a secure world (SW), where SW has direct access to resources in NW, but NW cannot directly access SW. Instead, any access to the SW must go through the secure monitor in the monitor mode via a secure monitor call (SMC). The secure monitor determines whether to switch the CPU mode to SW and grant access to the resources in SW by following a access control policy.
TWO-WAY REAL TIME MULTIMEDIA STREAM AUTHENTICATION USING PHYSICAL UNCLONABLE FUNCTIONS
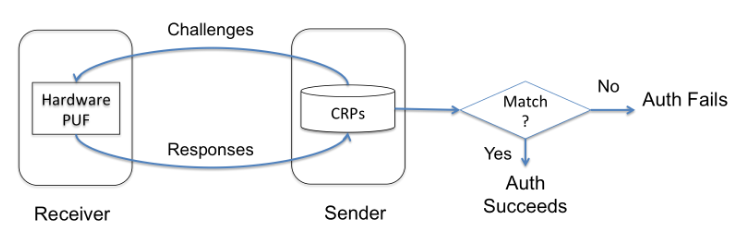
Figure 5.1: Flow of The Device Authentication Protocol
In device authentication our goal is to let the sender determine whether the receiver device, which is requesting the video stream, is a registered device that has permission to view the surveillance video. Figure 5.1 illustrates the authentication protocol to achieve the goal leveraging PUFs. There is one PUF involved for each pair of sender and receiver, and the PUF is physically possessed by the receiver. The sender hosts a secure database that contains a sufficient set of CRPs corresponding to the receiver’s PUF. There are several ways in which the sender could initialize the CRP database.
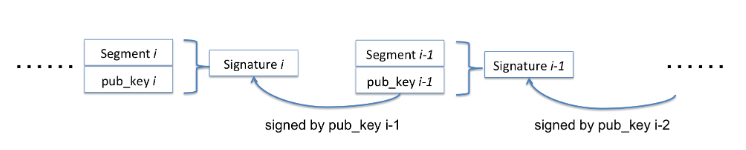
Figure 5.2: Flow of The Chaining-based Signature Scheme for Multimedia Authentication
For multimedia content authentication, i.e., verifying the integrity of the stream, we adopt the hash chaining method proposed by Gennaro and Rohatgi with our improvement based on PUF. We first split the video stream into continuous streams, which is compliant with the existing HTTP video streaming mechanisms. Then, for each segment i, proposed to embed a one-time public key and the one-time signature of itself with respect to the key contained in segment i − 1. In this way, there will be a chained signing and verifying procedure as shown in Figure 5.2.
EXPERIMENTAL RESULTS
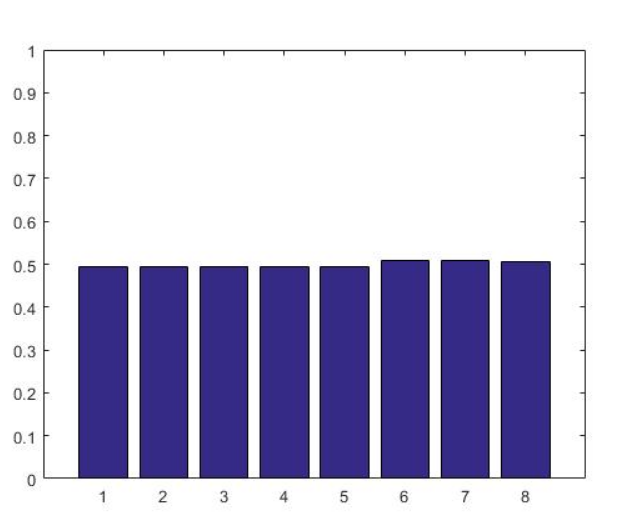
Figure 6.1: Probability of 0s in Each Position of The Response
We also evaluate the possibilities of 0s and 1s in each bit of the response for the 5000 CRPs. Ideally, the probabilities of 0s and 1s should be 50%. Figure 6.1 shows the probability of 0s in our evaluation, which is close to the ideal results.
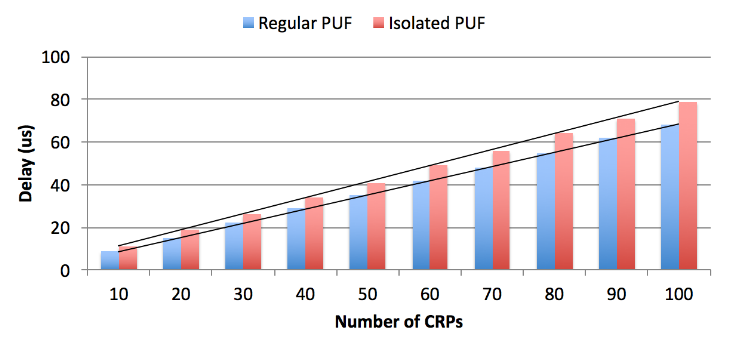
Figure 6.3: PUF Timing Evaluation results
Figure 6.3 shows the timing evaluation results comparing the isolated PUF with the regular PUF without hardware isolation 1. We observe that the isolated PUF demonstrates only slight performance overhead as compared to the regular PUF, which is due to the world switching delay and the load/store operations to access the shared memory.
CONCLUSION
In this study, we have developed a hardware isolation-based approach to protect PUFs from security attacks. In particular, we embedded the target PUF in a physically isolated secure environment, as enabled by the ARM Trust Zone technology, which prevents the attacker’s direct access to the PUF. Also, we deployed an access control policy to prevent unauthorized or excessive requests to the PUF, to prevent modeling and DoS attacks. Furthermore, we showed that PUF as a hardware security primitive can be used in a multimedia streaming application to provide both device and multimedia content authentications. Our system implementation and experiments on Xilinx Zedboard verified the security and performance of the proposed approach.
For the future work, it is very interesting to look into the FPGA fatigue patterns as it changes the paths of design in passage of time. Therefore, the responses to challenges might be different from what we currently observe. Also, it will be interesting to conduct a more intensive study and evaluation on the resilience of PUF against a broader set of threat models.
Source: University of Nebraska – Lincoln
Author: Mehrdad Zaker Shahrak