ABSTRACT
Industrial Control Systems ICS which are pervasive in our nation’s critical infrastructures, are becoming increasingly at risk and vulnerable to internal and external threats. It is imperative that the future workforce be educated and trained on the security of such systems. However, it is equally important that careful and deliberate considerations must be exercised in designing and implementing the educational and training activities that pertain to. To that end, we designed and implemented pedagogical materials and tools to facilitate the teaching and learning processes in the area of ICS security. In this paper, we describe those resources, the professional development workshop to disseminate the curriculum materials, and the evaluation results pertaining to those artifacts and activities.
BACKGROUND AND MOTIVATION
With an ever – increasing part of our nation’s critical infrastructures (CIS) in the hands of public and private employees via computer systems, the need for a cyber security educated future workforce in cyber security has never been so great. our critical infrastructures, such as power grid, transportation, drinking water, wastewater treatment, and defense systems, find themselves increasingly vulnerable to internal and external threats that can cause serious damage to our economy and well being.
Since the operation of these infrastructures is heavily dependent on control systems, it is imperative that the future workforce be educated and trained on the security of such systems. However, it is equally important that careful and deliberate considerations must be exercised in designing and implementing the educational and training activities that pertain to CIS security.

Figure 1. The Industrial Control Systems Toolkit.
Programmable Logic Controller (PLC) programming, control system networks and protocols, control system vulnerability assessment and penetration testing and defensive techniques and incident response for control systems. Further more, for each module, we provided hands – on laboratory projects that introduced the Problem Based Learning (Hung, Jonassen, & Liu, 2008) approach to learning and enabled the participants to practice the technique before applying it in their classrooms. These laboratory exercises were conducted using a control system toolkit, shown in Figure 1, which was designed guided by the fundamental concepts of simplicity, modularity, and portability.
DETAILS OF THE LABORATORY PROJECTS
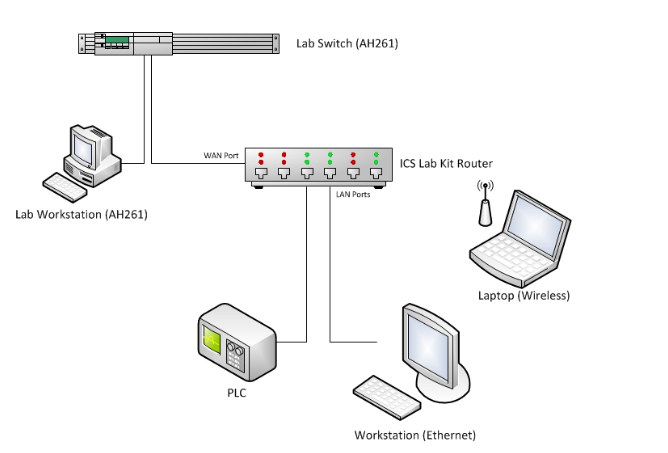
Figure 3. The Defensive Security Equipment Setting.
A simple HMI program has been provided with this exercise, along with the corresponding ladder logic firmware. After the PLC has been configured and tested, the router in the ICS lab kit is configured to accept remote SSH connections, and message logging is enabled. Once this has been accomplished, the firewall is configured at the command line using IPTABLES. After completing the desired configuration, it is made permanent and readily available by creating a firewall configuration script. Specifically, each participant is required to perform the following:
- Configure the router firmware for remote shell access and event logging
- View and analyze the default firewall configuration
- Open a Modbus connection to the PLC within the LAN
- Add and test a firewall rule to allow Modbus connections from the WAN
- Add and test a rule to block Modbus connections from a specific WAN host
- Add and test a rule to block all Modbus traffic from the WA
- Add and test a rule to enable auditing of successful and unsuccessful Modbus connection attempts from the WAN
The equipment setting for this laboratory exercise is depicted in Figure 3.
PROJECT EVALUATION
The evaluation plan includes a mixed methods approach utilizing both qualitative methods prescribed by Patton (2002) and quantitative methods prescribed by Creswell (2005) to guide the formative and summative evaluation procedures. Formative evaluation procedures assure continual improvement of the project, and summative evaluation procedures assess project objectives and implementation.
EVALUATION SUMMARY
Overall, the pre and post – workshop surveys indicate that the topics for the workshop were well chosen and well delivered, and the toolkit was rated as excellent. The results highlight that Industrial Control System Security is a topic that is not well – covered in computer science curricula and the workshop, as intended, highlighted the importance of that and other aspects of cyber security and provided instructors with tools (the toolkit and the laboratory activities) to integrate control system security into their courses.
CONCLUSION AND FUTURE PLANS
In this paper, we argued for the critical need for an educated workforce that is trained in industrial control systems security. We also reported the ICS curriculum modules and the laboratory exercises that were disseminated to a group of college instructors in a professional development workshop during the summer. The evaluation results that were gathered prior and after the workshop highlight the following notable pedagogical facts and outcomes:
- ICS security is not a part of the information security curriculum in college;
- The curriculum modules and the related laboratory projects were overwhelmingly well received.
- The pedagogical materials on ICS security will be integrated by the participants into their respective security curriculum
- The ICS toolkit was rated very positively and will greatly benefit and enhance the participants’ existing infrastructure. Future plans, connected with these activities and toolkit, are the following.
- The enhancement of the toolkit to include a Raspberry Pi for Internet of Things (IoT) security, and
- The development of additional curriculum modules in the areas of deep packet inspection of other ICS network packets that are not previously covered, secure programming in ICS program development, and threat intelligence/kill chain model for ICS security.
Source: Jacksonville State University
Authors: Guillermo A . Francia III | Greg Randall | Jay Snellen
>> 200+ IoT Led Engineering Projects for Final Year Students