ABSTRACT
IoT device forensics is a difficult problem given that manufactured IoT devices are not standardized, many store little to no historical data, and are always connected; making them extremely volatile. The goal of this paper was to address these challenges by presenting a primary account for a general framework and practical approach we term Forensic State Acquisition from Internet of Things (FSAIoT).
We argue that by leveraging the acquisition of the state of IoT devices (e.g. if an IoT lock is open or locked), it becomes possible to paint a clear picture of events that have occurred. To this end, FSAIoT consists of a centralized Forensic State Acquisition Controller (FSAC) employed in three state collection modes: controller to IoT device, controller to cloud, and controller to controller.
We present a proof of concept implementation using openHAB – a device agnostic open source IoT device controller – and self-created scripts, to resemble a FSAC implementation. Our proof of concept employed an Insteon IP Camera as a controller to device test, an Insteon Hub as a controller to controller test, and a nest thermostat for a a controller to cloud test. Our findings show that it is possible to practically pull forensically relevant state data from IoT devices. Future work and open research problems are shared.
IOT FORENSIC CHALLENGES
The next subsections present research on wearable IoT forensics, mobile forensics and IoT forensics reviews logs and how they are used in digital forensics and discusses IoT controllers. It is of note that at the time of writing, literature on IoT forensics was sparse.
- Wearable IoT forensics
- Mobile device forensics
- Logs
- IoT forensics
IOT FORENSIC CHALLENGES
With the dawn of the IoT age and advancements made in nearly every aspect of digital systems, we have reached a critical tipping point in the world of digital forensics. points out that many of the tools and techniques that once worked without question are quickly becoming obsolete. File formats for storing forensically relevant data are becoming proprietary often requiring complex reverse engineering efforts. Data is often split into many elements and stored in the cloud. There are also legal challenges which limit data investigators are able to gain access to.
FSAIOT FRAMEWORK
The Forensic State Acquisition from Internet of Things (FSAIoT) framework consists of a centralized controller which we title Forensic State Acquisition Controller (FSAC) and three state collection methods where state refers to the current state of an IoT device (e.g. door open or closed). The three methods or modes are as follows: (1) controller to IoT device (2) controller to cloud, and (3) controller to controller. Together, these three modes allow for the state acquisition of a multitude of IoT devices. In order to realize / implement the FSAC, we analyzed existing IoT controllers to provide a brief overview of existing solutions and motivate why we implemented our FASC using openHAB.

Figure 1: FSAC to Device connection.
Often, IoT device connections are construed as a plain controller to device type connection shown in Figure 1. A simple example would be an IP camera and an application residing on a computer within the same network used to control it. When a camera detects motion it can be registered as a state change. This state change can be reported back to a listening controller where further actions can be taken based on the identified state change.
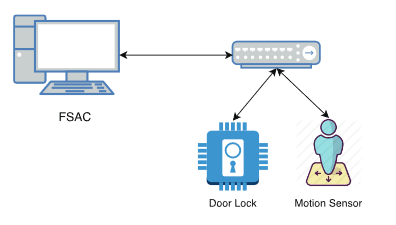
Figure 3: FSAC to controller.
As mentioned before, controllers connect back to the Internet to allow for simple control via mobile applications or web interfaces. Thus, it is possible to go from a FSAC to a controller as shown in Figure 3. By accessing the controller, the states of multiple devices can be acquired. Obviously, this stands to be a lucrative data collection point in our framework. As companies expand their suite of IoT devices, the need to maintain a central point of control is cultivated. This centralized point of control also promotes a consolidated interface for collecting state data of multiple devices.
FSAIOT FRAMEWORK PROOF OF CONCEPT IMPLEMENTATION
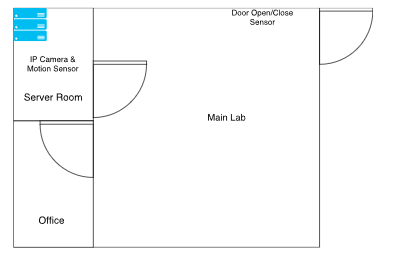
Figure 4: Lab scenario layout showing IoT device locations
In Figure 4, the facility and its layout are illustrated. This layout could have been obtained perhaps by public access records or during an initial set up or reconnaissance of the facility. Knowing what IoT devices are available and where they are located is important to help map out events that occurred.
DISCUSSION
Our findings show that indeed IoT device state and or the state change could be of forensic value. To substantiate our claim, queries were performed to show both the current trend in IoT devices and what sort of access might be available for these devices. With that said, our method, provides a general solution towards device state acquisition it does not physically acquire the memory of the devices themselves. If we switch focus to the future of our proposed approach, it becomes important to understand the future of APIs in the IoT domain.
LIMITATIONS
The biggest limitation both in IoT forensics and with the FSAC prototype is accessing historical and deleted data. Currently, the FSAC proof of concept can pull the state of the nest thermostat. However, the Insteon door sensor and motion sensor will only allow the acquisition of the change of state as mentioned. The second challenge lies in the need for physical access. This is a common challenge with regards to digital forensics and security.
CONCLUSION
In this work we argued that there are many challenges related to IoT device forensics. We presented the FSAIoT framework, and illustrated its feasibility by implementing a proof of concept FSAC using OpenHAB as well as self-created scripts to validate the feasibility of the framework. We showed that we are able to reliably collect state data from IoT devices using the three different modes: controller to device, controller to cloud and controller to controller. Even considering the limitations, we contend that our proposed framework and FSAC proof of concept are essential steps in evolving a general methodology for obtaining valuable forensic evidence from a diverse and thriving climate of IoT devices.
Source: University of New Haven
Authors: Christopher S. Meffert | Devon R. Clark | Ibrahim Baggili | Frank Breitinger
>> Latest Sensor based IoT Projects for Engineering Students
>> Latest 50+ IoT based Security Projects for Engineering Students